This fifth annual benchmarking report provides information and research on security, environmental, and financial issues related to IT Asset Disposition (ITAD) and the more general IT Asset Management (ITAM) discipline.
This report was built from data Cascade compiled through (1) a November 2018 customer survey, (2) an evaluation of more than 500,000 assets processed by Cascade in 2017 and 2018, and (3) a review of related industry research.
As a benchmarking tool, we encourage you to use the information to help understand how your ITAM/ITAD program compares to others and how you can further improve your systems to better attain your desired outcomes.
Read more about the survey respondent demographics.
| IT Asset Management Programs |
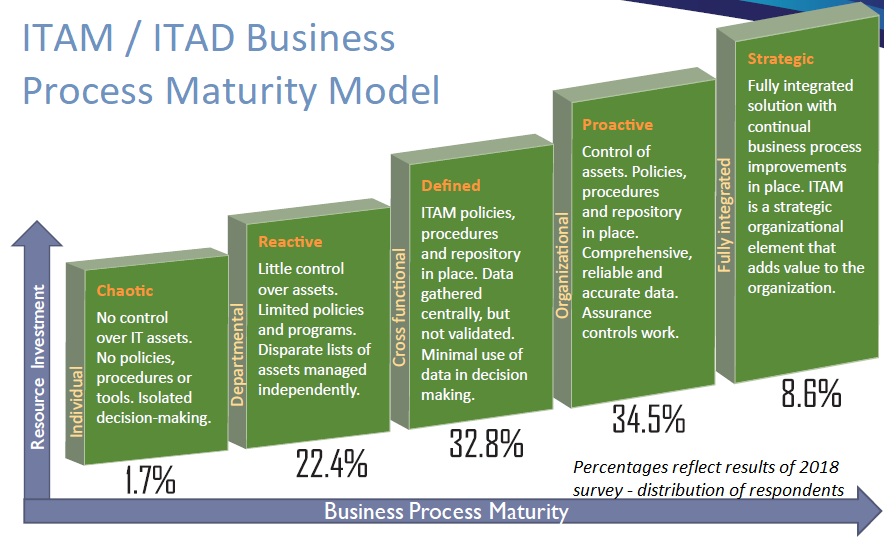 Organizations find themselves in different development stages of their IT Asset Management and Asset Disposition programs based on the complexity of their systems and the resources they can allocate to this process. These different stages are illustrated in the Maturity Model graph. Ideally, as an organization’s ITAM program matures, the total cost of IT ownership and security risk from data loss are both reduced while more strategic value is generated by the IT assets.
Organizations find themselves in different development stages of their IT Asset Management and Asset Disposition programs based on the complexity of their systems and the resources they can allocate to this process. These different stages are illustrated in the Maturity Model graph. Ideally, as an organization’s ITAM program matures, the total cost of IT ownership and security risk from data loss are both reduced while more strategic value is generated by the IT assets.
In our survey, we asked “What stage of the ITAM/ITAD Process Maturity Model would you place your organization in?” This year’s response distribution is listed under the bar graph. Firms show an improvement in their programs compared to the previous year.
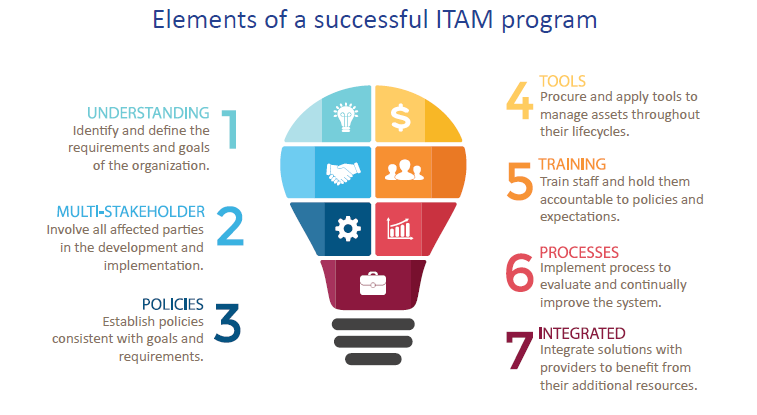
Effective IT asset disposition begins with a coordinated IT Asset Management process. Successful ITAM strategies help organizations generate value from their IT assets and reduce risk. The IT Asset Manager is responsible for managing the disposition vendor, ensuring personally identifiable information is destroyed, and reporting asset status for financial accounting.
Cascade has found that the most effective ITAM programs involve stakeholders from IT, risk management, facilities, environmental health & safety, finance and procurement. Because the CIO and other executives of an organization can be personally liable for the improper disposition of IT assets and loss of data during disposal, it is a good idea to include them in the ITAM program, too.
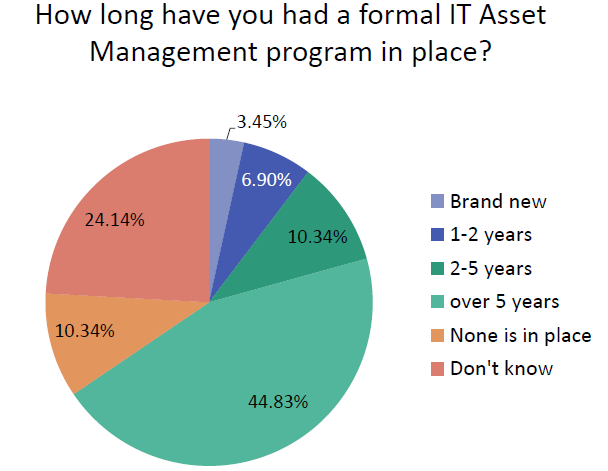
Most of our survey respondents indicate they’ve operated a coordinated ITAM program for more than two years.
While there are many issues to consider when setting up and managing an asset disposition program, we’ve found that people responding to our surveys consistently rank these five criteria in the same order year after year. “Security” is always the number one consideration for people setting up and managing ITAD programs.
All criteria saw a boost in importance this year, but “freeing up space” saw the greatest increase in score - a 6.5% increase. The other criteria grew at a rate of 1.5% to 2.0%.
Even though retired IT assets generate significant resale value, this is seen as the least important factor when making disposition decisions.
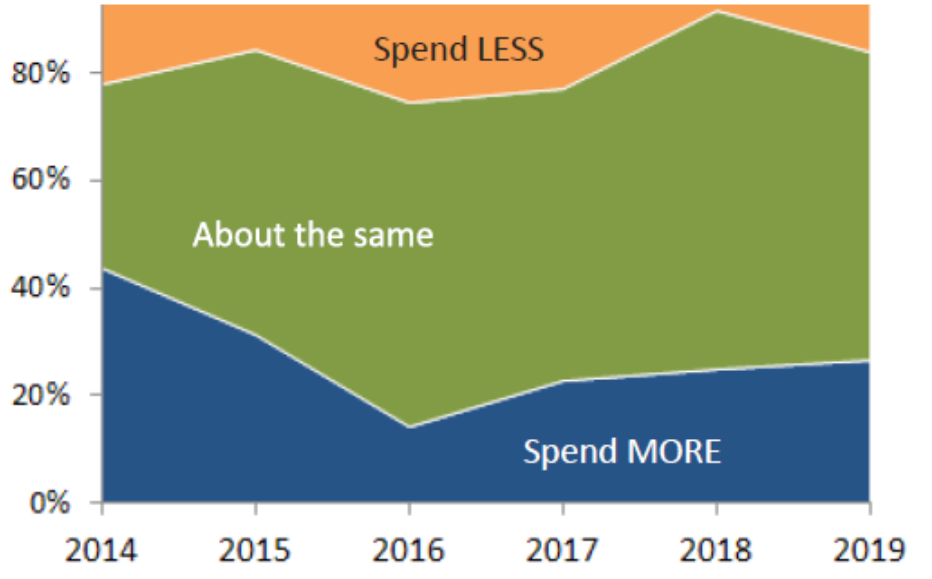
In this year’s survey, respondents indicated a slight increase in expectations to spend more (from 18% to 22%) on IT hardware in 2019 compared to 2018, but more than twice as many respondents (from 6% to 13%) plan to trim their spending in 2019. The industries starting to cut back are from the financial/banking sector, healthcare and government.
For desktops, 51.7% of respondents are now refreshing their devices every 4 years or less, compared to 53.1% in 2018. Almost half of respondents hold onto their desktops for 5 or more years now, the longest desktop refresh cycle we’ve recorded over five years.
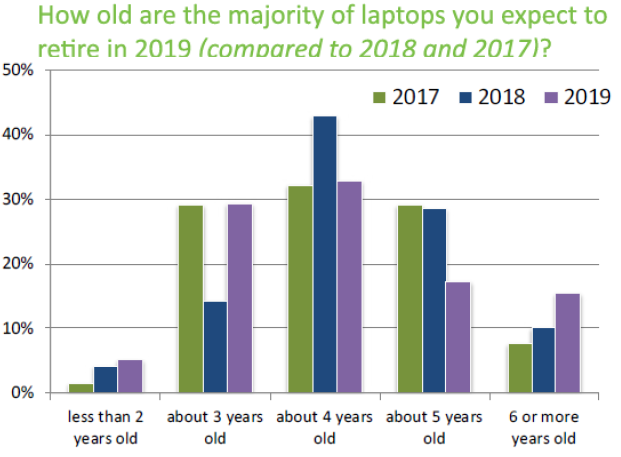
For laptops, the refresh rate is shortening. Respondents expect 67.2% of retired laptops to be 4 years old or less, compared to 61.2% in 2018 and 63.0% in 2017. Financial/Banking firms and companies providing IT services/software have the fastest laptop refresh rates.
For the third straight year, smartphone use continued growing at a double-digit pace. Company owned phones were provided to 13% more employees in 2018 and 25% more employees were expected to use their own phones for work (“BYOD”). Industries with above average smartphone adoption (when provided by the employer) are government, financial, and healthcare. BYOD adoption is led by healthcare, IT services/software, and insurance industries.
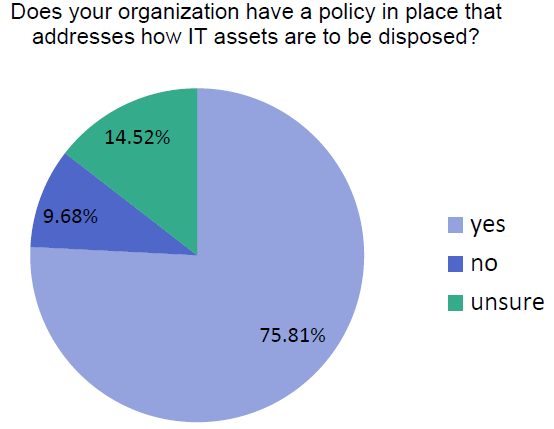
Over 75% of respondents indicated their organization has a policy in place that addresses how information on IT assets are to be destroyed when disposed (10% don’t have a policy and the remaining 15% of respondents weren’t sure if they had a policy).
In some industries or jurisdictions, there are regulatory requirements to adopt a data destruction policy – and to follow it. When firms create a policy, its important to make sure it addresses risks to the organization. These can be threats to a loss of data at any stage in the process. A risk can also be from being found to be noncompliant with regulatory requirements – so be sure your policy is consistent with the regulations.
We asked respondents what is included in their security policy related to ITAD. The checklist to the right lists their responses.
Every item on the checklist should be included in a company’s data security policy and program. Most importantly, employees are expected to be informed and trained on the policy. Keeping a signed acknowledgment of the policy on file is the best way to demonstrate to auditors that you took reasonable efforts to train staff, which will prevent compliance fines and should also mitigate potential data breaches.
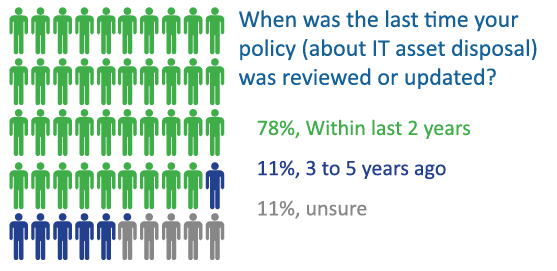
Most security regulations require security policies be “reviewed and updated as needed,” which typically means they should be checked annually. In fact, it is recommended that industries regulated by privacy protection programs like HIPAA, FACTA or PCI-DSS should review related security policies annually in order to stay current with changing regulations.
In addition, the types of assets an organization supports and the way they are used by an organization is evolving on a regular basis and may impact the policy. It’s a good practice to at least review the policy once per year or whenever major changes take place.
This year’s survey finds companies are more actively reviewing their policies. In 2017, only 60% of respondents reviewed their policy in the last 2 years. At least now we’re up to 78%.
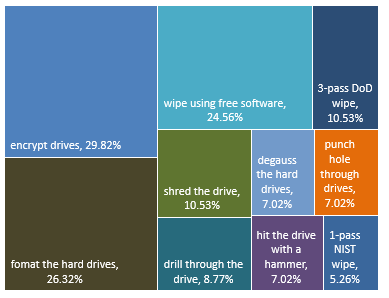
Organizations report that they may use one or more ways to control and destroy data on their hard drives before these devices leave their premises. Encryption of drives grew from 9% of respondents last year to 30% this year.
In this year's survey, 49% of respondents (down from 56% last year) didn't perform any onsite media sanitization themselves and instead outsourced all data destruction work to Cascade. Thirty-two percent placed media in a secure bin for offsite destruction.
Cascade recommends all organizations adopt appropriate methods of media destruction based on the NIST 800-88 Guidelines for Media Sanitization and consistent with their tolerance for risk. This may include performing some sanitization/destruction of media at your facility, setting up a secure chain of custody of the media to the final processor, and assuring that all data are properly destroyed and accounted for by the processor.
Special Media Sanitization
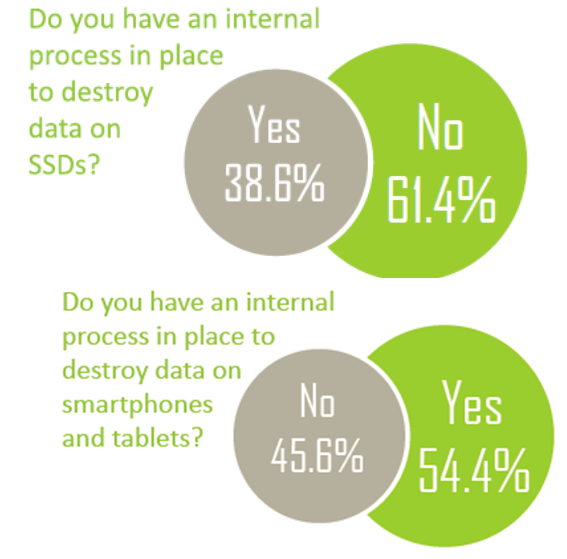
We also ask people if they have the capability and take the time to sanitize data from SSDs and flash media devices like phones and tablets.
This past year, we actually saw the percentage of firms that internally destroyed data on SSDs drop from 44.4% in 2017 to 38.6% in 2018. The percentage of firms that have an internal process for smartphone data destruction is a bit better than last year, climbing from 53.3% to 54.4%.
While Cascade is able to perform these data destruction processes consistent with NIST 800-88 Guidelines, it’s important for all organizations to be able to address data security concerns on these media whenever they are redeployed in the organization or potentially sent back to a phone carrier at the end of their use.
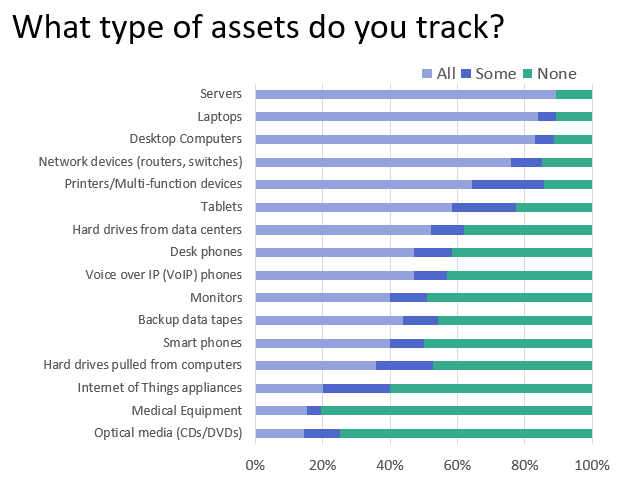
An important part of an asset management program is the tracking of assets.
When Cascade asked our survey respondents what they tracked in their asset management programs, servers jumped to the number one spot this year (up from #3 in the previous year), likely due to their asset value and security risk. Desktops, laptops and network gear come next.
Tracking data bearing assets to the point of final disposition is a requirement of privacy protection regulations. It is also an essential risk mitigation strategy. This is essentially the critical role of the IT Asset Manager. Assets need to be tracked throughout their use in an organization to mitigate security risk, manage licenses and the value of the assets, and ensuring the assets are productive.
When an asset isn’t tracked, you won’t know if it goes missing. Organizations needs to answer the question, “what is the risk of not knowing when an asset is lost?” to help determine the level of effort and investment to accurately track the asset until final disposition.
Privacy protection regulations impacting ITAD
For years, the HIPAA-HITECH Act has required Covered Entities to have a policy for the destruction of Personal Health Information and to put an agreement in place whenever outsourcing destruction activities to a Business Associate. You’re probably familiar with GDPR and the “right to be forgotten” requirement. That impacts data destruction. Last year, California also implemented the Consumer Privacy Act, which is similar to GDPR. Colorado’s new legislation is more specific about data destruction requirements. It went into effect on September 1, 2018 and creates more stringent requirements regarding the disposal of personal information. Under the law all “covered entit[ies] in the state that maintain paper or electronic documents during the course of business that contain personal identifying information” will be required to develop a written policy for the destruction or disposal of such information once such documentation is “no longer needed.”
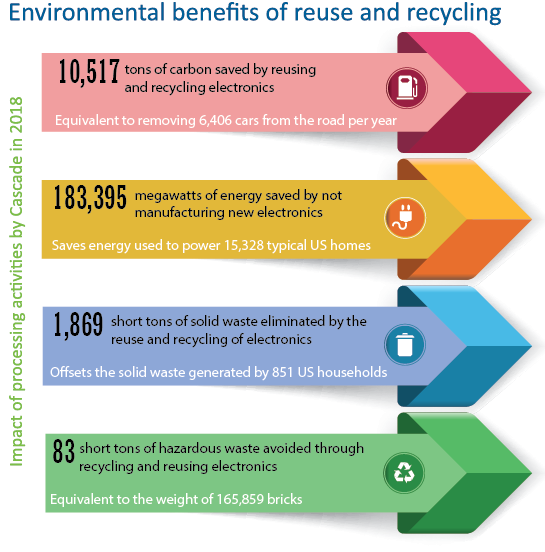
Each year, Cascade tracks the environmental impact of our reuse and recycling activities. This chart shows the collective impact from all the equipment processed by Cascade in 2018. This information is based on a carbon impact calculator built by the EPA.
Individual customers of Cascade can see the environmental impact of having their equipment processed for reuse and recycling. Just ask.
The cost of environmental noncompliance
State and federal regulators continue to step up enforcement of laws related to e-waste disposal. Both recyclers and generators of old electronics are receiving civil and criminal penalties. These consequences make it even more important to ensure your used electronics are processed properly and lawfully. Here are some incidents reported in 2018:
Target will pay $7.4 million to settle allegations it again broke California law by illegally tossing used electronics and hazardous materials into the garbage.
Whole Foods Market California and two companies it owns will pay over $1.6 million to settle allegations they improperly disposed of electronics and hazardous wastes.
A former executive of Global Environmental Services, an e-scrap processor in Kentucky, was sentenced to three years in prison after pleading guilty to hazardous waste-related crimes.
A federal judge sentenced the former head of Zloop, an e-scrap recycler, to 10 years in prison and more than $27 million in restitution to victims based on a series of fraudulent schemes.
Carbon credits gain currency
 Firms may wish to offset carbon emissions to meet voluntary sustainability goals or to fulfill cap-and-trade compliance obligations. A dozen states and some Canadian provinces now require certain industries to reduce or offset their carbon footprint.
Firms may wish to offset carbon emissions to meet voluntary sustainability goals or to fulfill cap-and-trade compliance obligations. A dozen states and some Canadian provinces now require certain industries to reduce or offset their carbon footprint.
A new program makes available certified carbon credit offsets resulting from the reuse of refurbished IT equipment. These credits are earned when used computers are refurbished and resold with a three-year warranty, replacing the need to manufacture a new computer that contributes an equivalent amount of CO2 when produced. Companies can use these credits to offset the carbon generated from purchasing new computers or the overall carbon footprint of the organization.
These computer reuse carbon credits are currently registered by the Canadian Standards Association to ensure these offsets are verifiable. The program is being managed by CarbonBank. Talk to Cascade to learn more about this program.

About "Zero Waste"
Many companies have a goal of "Zero Waste." It's difficult to expect to divert all the waste generated by an organization into recycling streams. Some items (like certain plastics and contaminated materials) just can't be recycled completely, and incineration creates its own waste and health problems.
By eliminating items that eventually become waste, and reusing/recycling everything else, firms and individuals will be best positioned to reduce waste from their "ecosystem." This optimizes the use of resources over theur lives.
Cascade tracks how much of the material we bring in from all our customers and measures the percentage that is refurbished and reused or recycled and coverted into new raw materials for use in new products. Since there can be waste throughout the recycling chain due to contamination of materials, we find this "recovery yield" a better measure of optimizing resource use. In 2018, Cascade's recovery yield is 86.5%, up from 85.1% in 2017.
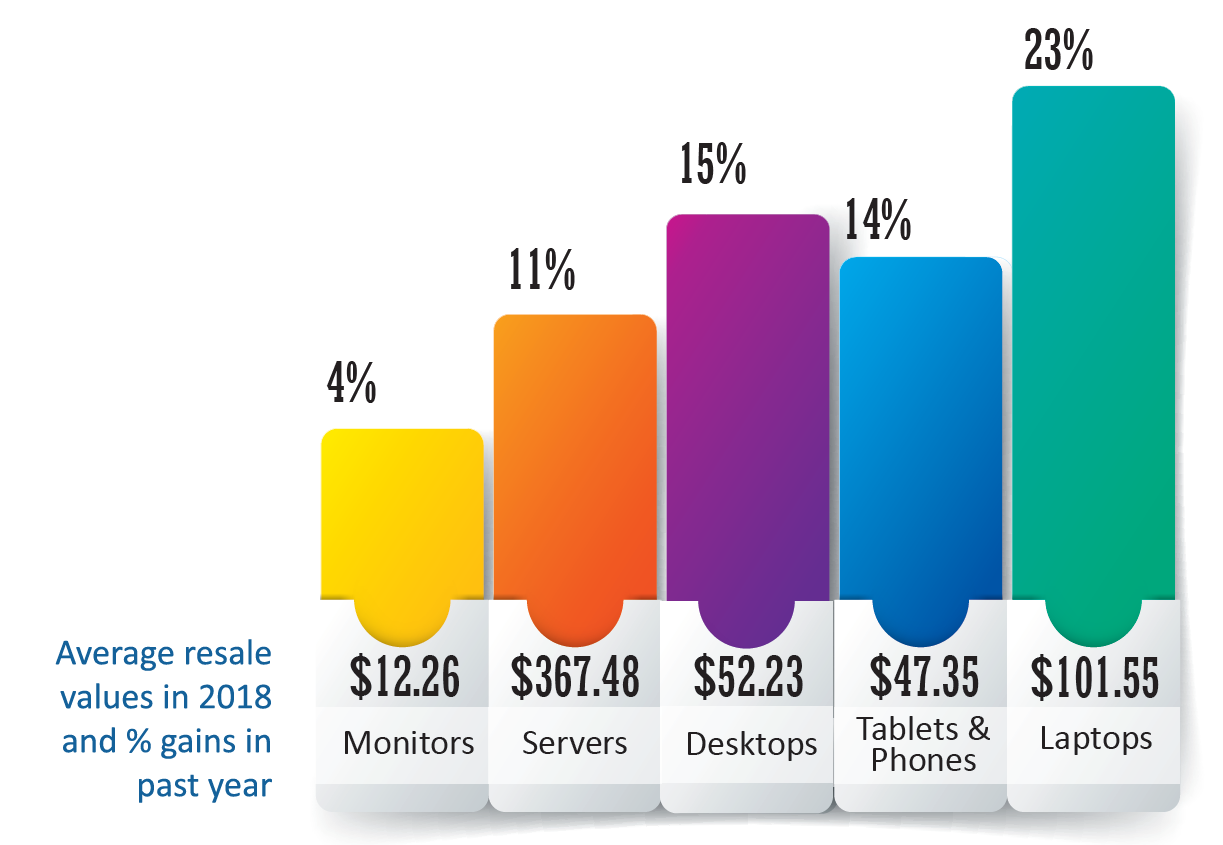
Cascade data analysis - 2018 ITAD Resale Values
One of the best ways to reduce ITAD costs is to maximize recovery values from retired equipment. In the past year, Cascade worked collaboratively with its institutional customers to cut net ITAD costs by 19%, primarily due to the 14% increase in the average price generated from the resale of Cascade refurbished equipment. Nearly all categories of products increased in value this year
This chart shows the average resale values for the most popular refurbished and resold products handled by Cascade for the past 2 years. There’s a lot of variability in the quality, configuration, models and condition of the equipment in all of these categories, but it provides some useful information on the relative resale value of different equipment and trends in their resale value. Plus, this includes hundreds of thousands of devices, so we have a pretty big sample size.
Applying the Circular Economy to ITAD
The Ellen MacArthur Foundation leads the charge to facilitate and formulate ideas and actions related to building circular economy systems. It involves global partners, including Google, Philips and companies from non-IT industries. A circular economy seeks to rebuild capital, whether this is financial, manufactured, human, social or natural.
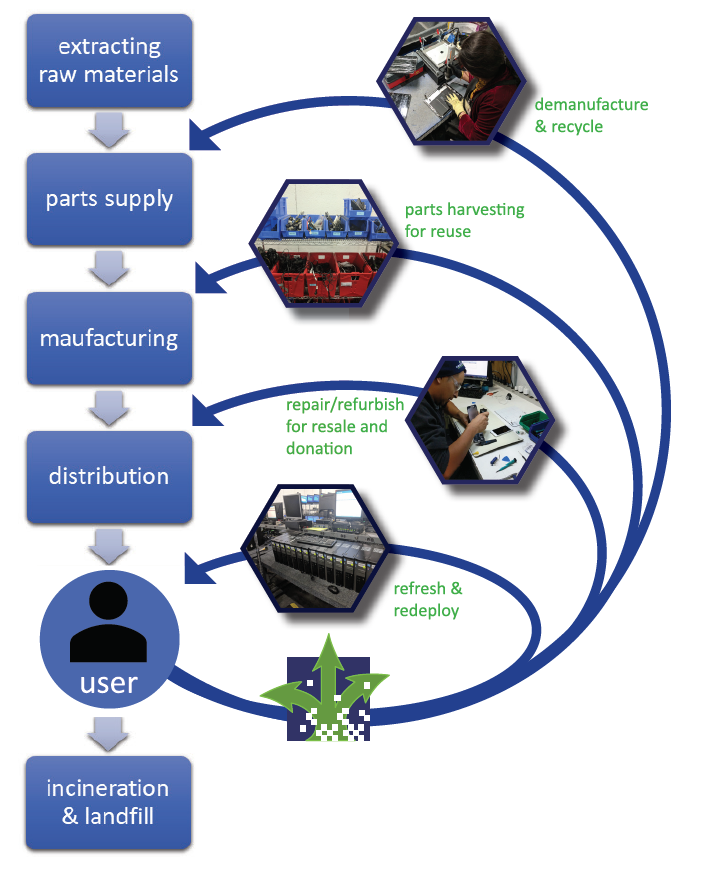
Businesses and organizations can adopt circular economy thinking into how they manage IT assets throughout their lifecycle. It starts with responsible procurement - purchasing devices that are suitable for the job, built to last, easily repairable, modular, upgradable, and designed for recycling. Some vendors now offer Device as a Service (DaaS) models which feature monitoring services to maximize up-time of the device by identifying when parts need repair or replacement before the entire device breaks down and is thrown away. When it’s time to cascade the device to another use, responsible IT asset disposition can look for options outside the organization to generate more value from reuse or recycling.
The role of the ITAD provider in a circular economy: When the organizational user is done with its “first use” of an IT asset, it can hand over the product to an ITAD provider which can cascade the device to its next best use. Providers like Cascade offer redeployment, refurbishment, reuse, parts recovery and recycling services. In addition, they can apply security tools to sanitize the data from devices. By integrating these functions into the lifecycle of IT assets in your organization, you can extract the most value from your devices, reduce procurement costs and mitigate the negative environmental burden of these products in the waste stream.