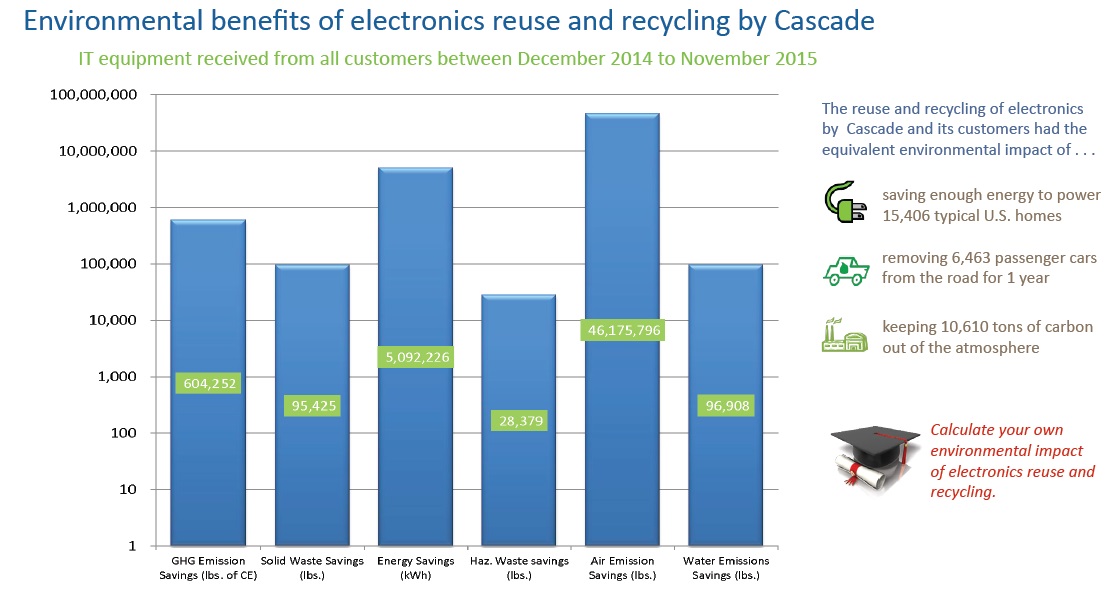
This second annual benchmarking report provides information and research on security, environmental, and financial issues related to IT Asset Disposition (ITAD). It also includes an overview of the NIST Media Sanitization Guidelines and illustrates best practices in data destruction for a wide variety of storage media.
This report was built from data Cascade compiled through (1) a December 2015 customer survey, (2) an evaluation of more than 200,000 assets processed by Cascade in the past twelve months, and (3) a review of related industry research.
The ITAD industry is expected to confront serious obstacles in 2016. Diminished recycling scrap values, increased regulatory scrutiny, and pressures to reduce costs all threaten the ability for processors to operate successfully.
Despite these challenges, Cascade was able to demonstrate a savings of 27.4% in net costs for its clients last year. This accomplishment was due to more aggressive repair and refurbishment activities, which generated greater resale revenues. In addition, Cascade collaborated with clients on smart cost containment programs.
This report presents information and insights gained from research and experience to help more organizations reduce their ITAD costs while ensuring their security and environmental interests are protected.
| IT Asset Management Programs |
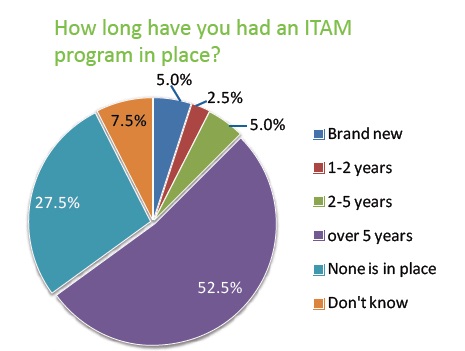
Effective IT asset retirement begins with a coordinated IT Asset Management process. Successful ITAM strategies help organizations generate value from their IT assets and reduce risk. The IT Asset Manager is responsible for managing the disposition vendor, ensuring personally identifiable information is destroyed, and reporting asset status for financial accounting. Cascade has found that the most effective ITAM programs involve stakeholders from IT, risk management, facilities, environmental health & safety, finance and procurement. Because the CIO and other executives of an organization can be personally liable for the improper disposition of IT assets and loss of data during disposal, it is a good idea to include them in the ITAM program, too.
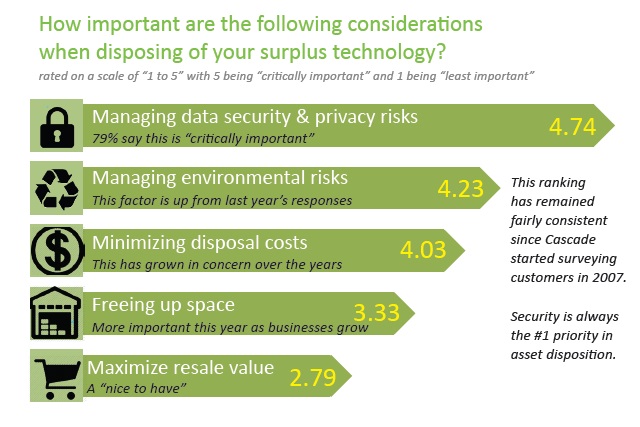
Each year, we ask survey respondents how important different criteria are when selecting an ITAD provider. This question is the same as the question Gartner asked its clients in the past. The answers over the years and between our survey and Gartner's are extremely consistent. While we know that cost is important to our clients, they don't want to skimp on service and protection if it means exposing themselves to more security risks or potential environmental liability.
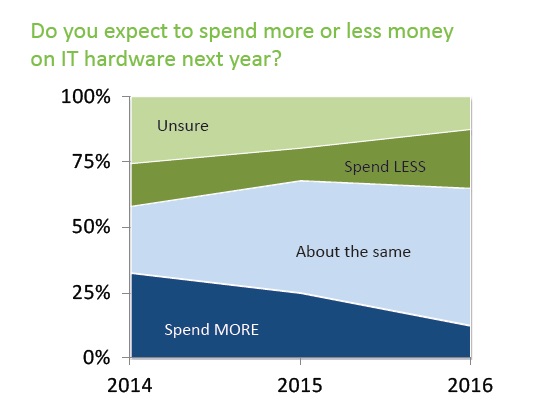
There's been a significant decline in the expectation to spend more on IT hardware each year (from 32.7% in 2014 to 12.5% in 2016). As a result, IT asset managers are challenged to find ways to stretch their budgets.
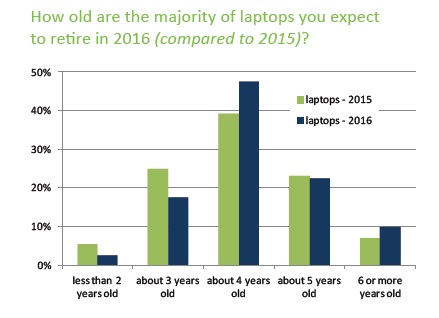
Survey respondents are planning to extend the refresh rates of their laptops and desktops hoping this will save costs. Cascade’s report on minimizing TCO shows this may not be an effective cost cutting strategy and will cost companies more in the long run.
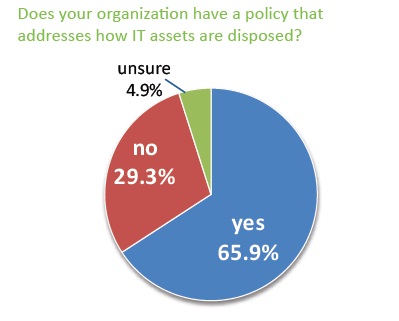
Many industries are regulated by some type of Privacy Protection Rule such as HIPAA or FACTA. Firms are also audited to voluntary standards which require that the organization have a robust security policy and an effective program in place to destroy data on retired devices. 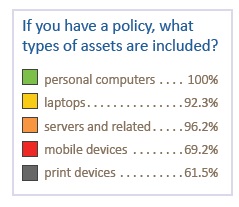
To be effective, security policies should address specific elements, such as employee training, vendor management, and data sanitization standards. A policy is an important tool for setting consistent standards throughout the organization. When enforced, the policy helps prevent data breaches and demonstrates the organization took reasonable precautions to prevent a loss of data.
Every item on the clipboard (side/below) should be included in a company’s data security policy and program. Most importantly, employees are expected to be informed and trained on the policy. Keeping a signed acknowledgment of the policy on file is the best way to demonstrate to auditors that you took reasonable efforts to train staff, which will prevent compliance fines and should also mitigate potential data breaches.

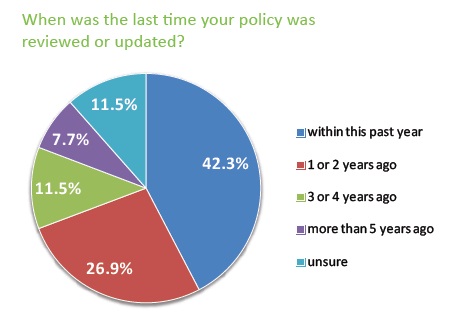
Most security regulations require security policies be “reviewed and updated as needed,” which typically means they should be checked annually. Be sure to conduct a threat assessment against your current asset base to ensure data protection and destruction programs are current and effective.
In 2016, the US Health and Human Services Office of Civil Rights will be auditing healthcare providers and will be looking for evidence of a policy.
Which methods do you use (internally) to control and destroy data on hard drives?
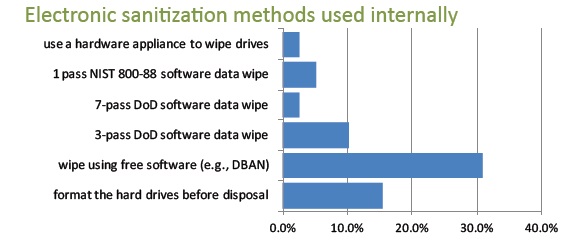
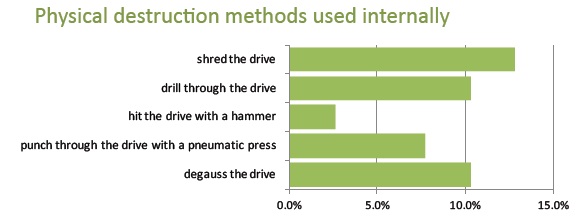
Organizations report that they may use one or more ways to control and destroy data on their hard drives before these devices leave their premises. Interestingly, a significant number (43.6%) report they do not use any internal controls on their hard drives. Instead, they rely on Cascade as their asset disposition partner to perform all data destruction on their behalf.
Cascade recommends all organizations adopt appropriate methods of media destruction based on the NIST 800-88 Guidelines for Media Sanitization and consistent with their tolerance for risk. In addition, actively tracking assets through tools like Computrace/Absolute DDS contributes to a more secure chain of custody of assets through final disposition. Cascade helps companies de-activate Computrace enabled devices as part of the disposition process.
Special Media Sanitization
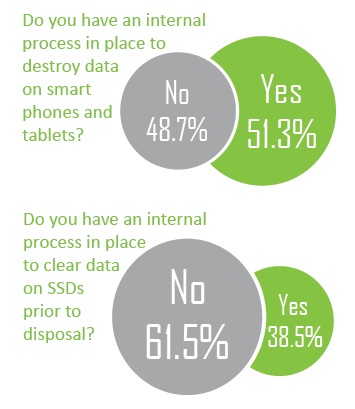
Different technologies are required to destroy data on Solid State Devices (SSD) and flash media in many tablets and smart phones. Our survey indicates many firms are still looking for processes to sanitize these media and responses are virtually identical to last year’s survey.
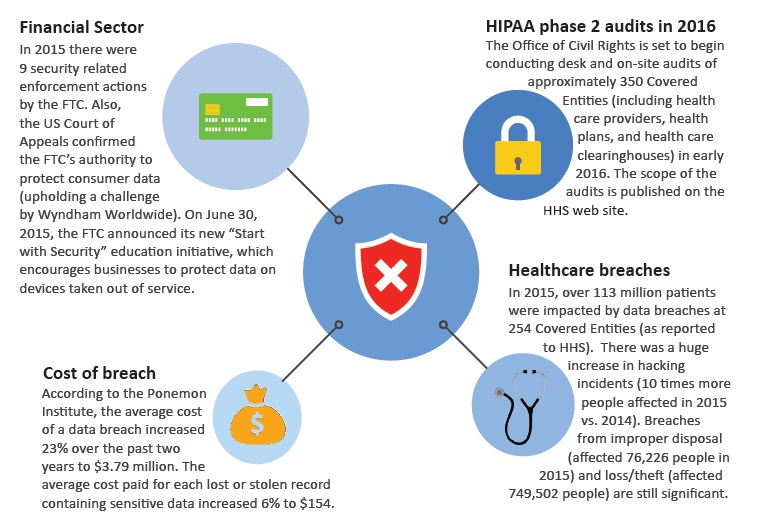
Data breach incidents - something to avoid!
There are now plenty of examples to justify investments in security controls and disposition programs. Increased penalties and regulations require organizations to implement ITAD strategies that seek to prevent and limit the loss of consumer and patient data.
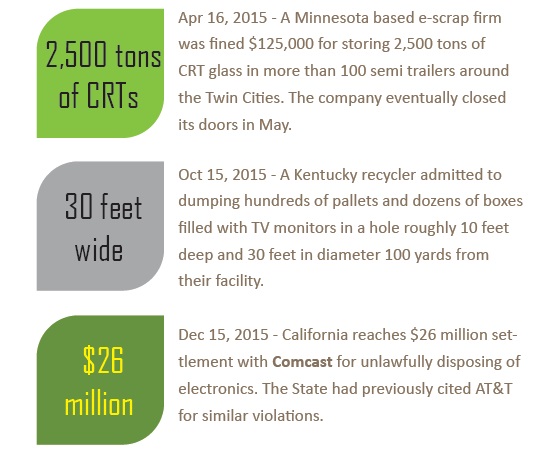
Illegal disposal now attracting regulators.
There were a number of prominent cases in 2015 involving civil and criminal penalties against businesses engaged in the illegal dumping of e-waste. Expect more incidents in 2016.
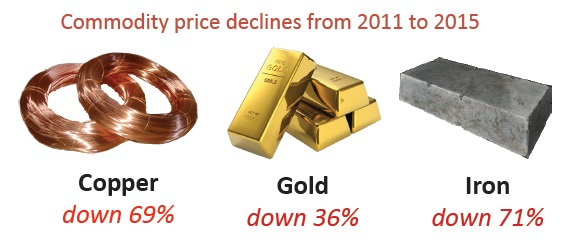
Low recycling values create challenges
While the U.S. economy may seem to be humming along, the value of scrap metals harvested from electronics has dropped dramatically from its peak in 2011. This is due to slower economic growth in China and Europe, a strong dollar valuation, and a glut of copper, aluminum and precious metals on the market.
At the same time, the costs for handling the hazardous materials in electronics are increasing. Compliance costs and the lack of markets for leaded glass and mercury products make it more difficult and costly to find good homes for these materials. It is expected that the situation won’t get any better through 2016.
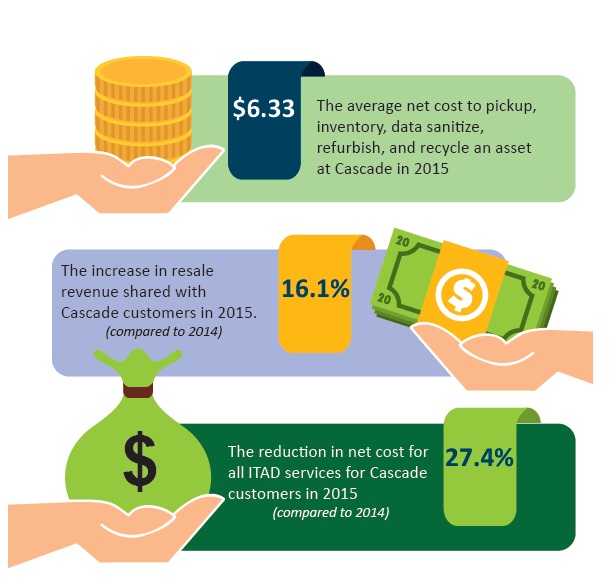
Cascade data analysis - 2015 ITAD costs
One of the biggest complaints with IT Asset Disposition programs is the cost. So how much does it cost to outsource ITAD services to a professional ITAD firm? For Cascade, the cost is dependent on what value added services you select and whether these costs can be offset by revenues generated from the resale of equipment.
While your disposal policy should dictate your security and environmental processing requirements, there are steps every organization can take to reduce disposition costs or turn this process into a revenue generator.
Companies that maintain a regular 3-4 year refresh program, allow for the resale of reusable equipment, and maintain their equipment while in use, will generally see most (if not all) of their disposition costs covered by revenue offsets.
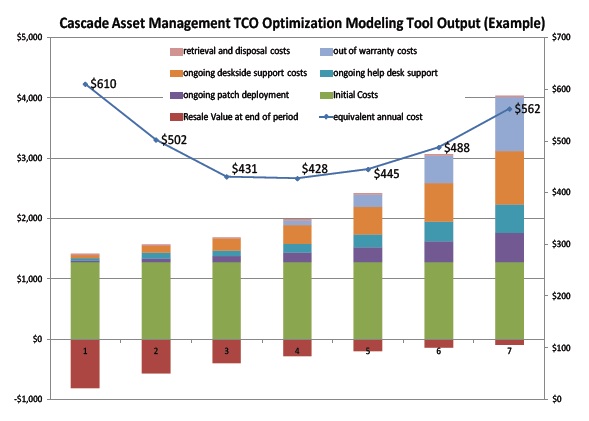
Maximizing asset value through its lifecycle
The best way to optimize the value of your IT assets is to consider their entire life cycle benefits and costs.
First, understand the value the assets provide to your organization, employees and customers. When IT assets are productive and well suited for their role, they demonstrate a positive impact.
Then, identify the costs to purchase, maintain and dispose of those assets. The value generated from the resale of working excess assets helps to offset these costs.
Taken together, you can determine the optimal refresh rate that results in the lowest average annual cost for your IT assets.