Many industries are regulated by some type of Privacy Protection Rule such as HIPAA or FACTA. For those organizations not required to comply with a particular security regulation, these privacy rules and the NIST 800-88 Guidelines for Media Sanitization provide a helpful framework for developing a data destruction policy and program. All industries can benefit from a robust security program that includes the destruction of data when assets are retired.
We asked respondents what is included in their security policy related to ITAD. The checklist to the right lists their responses.
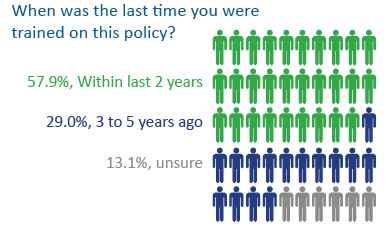
Every item on the checklist should be included in a company’s data security policy and program. Most importantly, employees are expected to be informed and trained on the policy. Keeping a signed acknowledgment of the policy on file is the best way to demonstrate to auditors that you took reasonable efforts to train staff, which will prevent compliance fines and should also mitigate potential data breaches.
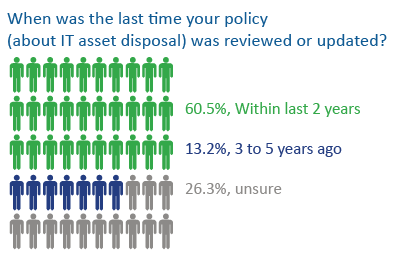
Most security regulations require security policies be “reviewed and updated as needed,” which typically means they should be checked annually. Be sure to conduct a threat assessment against your current asset base to ensure data protection and destruction programs are current and effective.
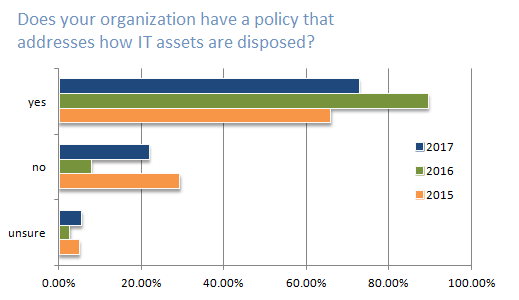
In 2016, the US Health and Human Services Office for Civil Rights audited healthcare providers and looked for evidence of a policy.
To be effective, security policies should address specific elements, such as employee training, vendor management, and data sanitization standards. A policy is an important tool for setting consistent standards throughout the organization. When people are consistently trained and security programs are enforced, the policy serves as an effective tool to prevent data breaches and demonstrates the organization took reasonable precautions to prevent a loss of data.