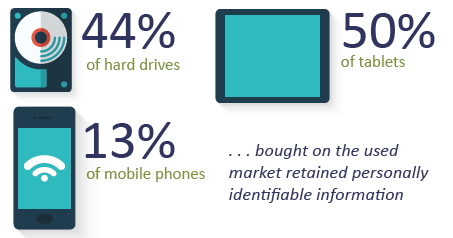
The National Association for Information Destruction (NAID) went out to resellers of used computer equipment to see how well data was destroyed on tablets, phones and hard drives before they were sold to the general public. They bought items from places like eBay, New Egg, and Amazon – resellers that may source this equipment from consumers and businesses. They found overall that 40% still retained some amount of personal information. A certified data destruction process, like Cascade’s, can greatly mitigate this risk.
Cascade recommends all organizations adopt appropriate methods of media destruction based on the NIST 800-88 Guidelines for Media Sanitization and consistent with their tolerance for risk. This may include performing some sanitization/destruction of media at your facility, setting up a secure chain of custody of the media to the final processor, and assuring that all data are properly destroyed and accounted for by the processor.
You don’t know what you don’t have, if you don’t track it.
In a survey of 181 large US corporations operating in the financial, healthcare, retail and utility sectors, Compliance Standards reported that 38% of enterprises say they can’t account for all their devices. They are essentially unable to verify whether these assets were properly retired, lost or stolen.
When Cascade asked our survey repondents what they tracked in their asset management programs, desktops, laptops and servers led the list (see table). At the same time, other devices that also contain data (smartphones, individual hard drives, VoIP phones, and data tapes) were tracked less often. New IoT products are managed even less.
Tracking data bearing assets to the point of final disposition is a requirement of privacy protection regulations, and it also an essential risk mitigation strategy.
Organizations report that they may use one or more ways to control and destroy data on their hard drives before these devices leave their premises. Still, many continue to use less effective destruction processes like drive formatting.
In this year’s survey, 56% of respondents didn’t perform any onsite media sanitization or destruction themselves and instead outsourced all data destruction work to Cascade.
Cascade recommends all organizations adopt appropriate methods of media destruction based on the NIST 800-88 Guidelines for Media Sanitization and consistent with their tolerance for risk. This may include performing some sanitization/destruction of media at your facility, setting up a secure chain of custody of the media to the final processor, and assuring that all data are properly destroyed and accounted for by the processor.
Special Media Sanitization
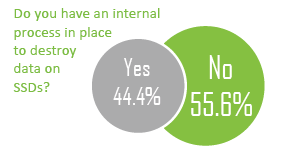
Different technologies are required to destroy data on Solid State Devices (SSD) and flash media in many tablets and smart phones. Our survey indicates many firms are still looking for processes to sanitize these media and responses are virtually identical to last year’s survey, though this is the first year a majority of respondents have sanitization programs in place.